Public-key Encryption | A look into the future

Technology is evolving and has the potential to break our current key-based encryption systems. What methods will we rely on to protect our data in the future?
Published by

Simone Catania
Date
As technology evolves rapidly, so must strategies for protecting sensitive information. Encryption, in particular, is an essential tool for safeguarding data from malicious actors. However, the recent growth in the transmission, collection, storage and processing of data, along with emerging technologies like cloud computing, 5G and the Internet of Things (IoT), have rapidly accelerated the transformation of the digital landscape. With each passing day, the magnitude and diversity of data transmission and storage are increasingly challenging the limits of traditional encryption methods and making more advanced encryption methods necessary.
This article explores future public-key encryption methods. Specifically, we delve into the critical problems of the current key-based encryption system and the drivers behind the transformation of encryption technology. We analyze the major innovations that have been developed to provide protection against modern-day cyber threats and highlight the potential vulnerabilities new encryption technologies must address. Finally, we aim to shed light on the role of encryption technology in safeguarding sensitive data, both now and in the future.
Where did public-key encryption originate?
The origin of encryption dates back to ancient times when it was closely linked with the study of cryptography, the study and practice of secure communication techniques. In the past, cryptography played a crucial role in military and intelligence forces. Ancient civilizations like the Egyptians and Romans used elementary encryption to transmit secret messages and protect sensitive information during wars and conflicts. Various methods, such as substitution ciphers, transposition ciphers and codes were utilized to hide the actual message from unauthorized individuals.
Over time, encryption techniques evolved alongside advancements in technology. From the era of manual encryption methods, modern encryption technologies emerged, leveraging complex algorithms, mathematical principles and the power of computers to ensure data security. Today, encryption has expanded beyond military use to encompass various applications across industries, governments and personal communication, protecting sensitive data and maintaining privacy in our increasingly digital world.
What is modern encryption?
Modern cryptography is rooted in computer science and mathematical functions, providing the foundation for securing data. Today, key-based encryption has become the standard practice for safeguarding digital communications.
The concept of encryption keys
The concept of using encryption keys is relatively straightforward. Encryption keys utilize algorithms to convert readable data into unreadable data, a process known as encoding. This transformation makes the data unintelligible to unauthorized individuals or machines attempting to access it. The receiver must use the corresponding decryption key to restore the data to its readable form. Encryption keys act as data guardians, preventing adversaries from subverting systems and misusing sensitive information.
Symmetric vs. asymmetric encryption
There are two types of key-based encryption, namely symmetric and asymmetric encryption. The difference lies in how the keys are used for encryption and decryption.
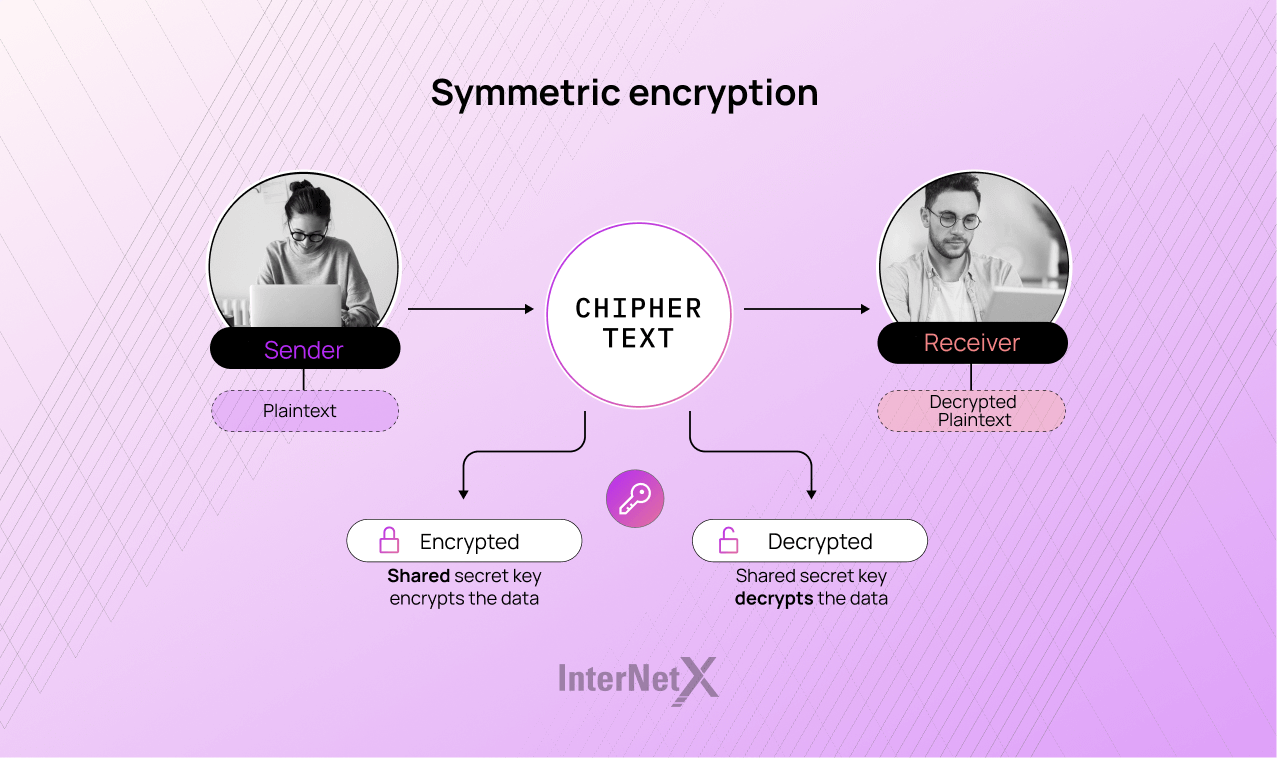
In symmetric encryption, the same key is used for both processes. This means the sender and receiver share a secret key to encrypt and decrypt the data. This symmetric key must be securely shared between the parties, as anyone who possesses the key can decrypt the data.
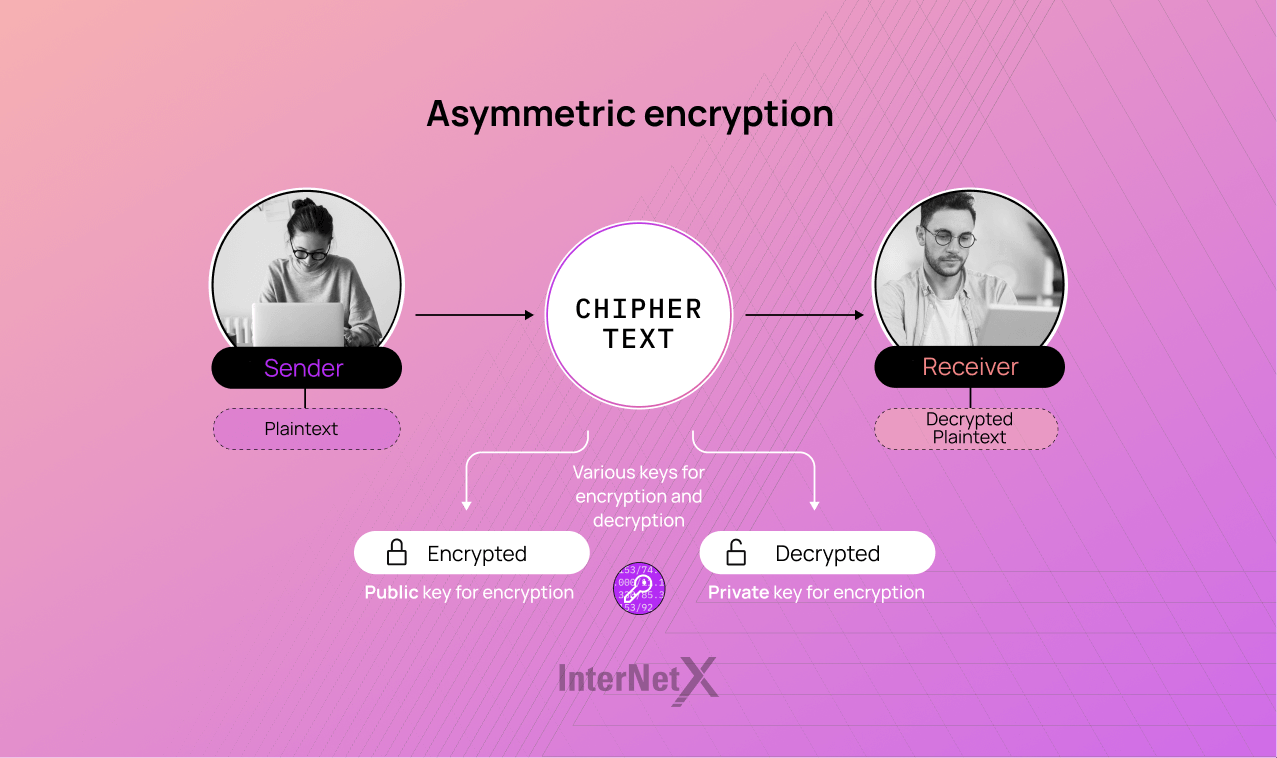
Asymmetric encryption, also known as public-key encryption, uses two different keys: a public key and a private key. The public key is openly shared and can be used to encrypt data, while the private key is kept secret and is used to decrypt the data. The key concept here is that the private key remains confidential and is not shared with anyone.
Symmetric encryption employs the same key, while asymmetric encryption employs two different keys, with the private key remaining confidential.
Strengths and weaknesses of key-based encryption methods
To fully grasp the significance of advancements in our current encryption system, it is essential to take a more detailed look at both the positive and negative aspects and the challenges that arise with the constant evolution of technology. For decades, organizations and individuals have trusted key-based encryption methods, which have proven to be the most effective solution for safeguarding sensitive data. However, as the landscape of data security continues to evolve rapidly, it has become crucial to thoroughly assess and analyze the strengths and weaknesses of these encryption methods.
Strengths of key-based encryption methods
- Historical adequacy: Key-based encryption methods have proven effective at providing data security. They have been widely implemented and have withstood numerous attempts to breach their defenses.
- Customizable security levels: Key-based encryption methods allow users to adjust the security level using longer keys or more complex encryption algorithms. This flexibility enables organizations to tailor the encryption strength to their needs.
- Efficiency: Key-based encryption methods are generally efficient and perform encryption and decryption operations relatively quickly. This makes them suitable for a wide range of applications for which speed is essential.
Weaknesses of key-based encryption methods
- Susceptibility to brute force attacks: Although the strength of key-based encryption depends on the key length and algorithm used, they are still vulnerable to attacks involving exhaustive key searches (brute force). As computing power is gaining strength continuously, the risk of successful brute-force attacks is increasing.
- Key management complexity: Keys can be challenging, especially in large-scale systems or when sharing encrypted data with multiple parties. Maintaining secure key management becomes increasingly difficult as the number of encrypted communications and devices increases.
- Single point of failure: If the encryption key is compromised, all encrypted data secured by that key becomes vulnerable. This single point of failure can expose sensitive information, making key-based encryption less effective in the face of determined attackers.
As data security threats grow in number and sophistication with technological advancement, exploring alternative encryption methods and solutions that address these weaknesses is essential. By considering the strengths and weaknesses of key-based encryption, organizations can make informed decisions to ensure the ongoing security of their data.
Data must be decrypted before processing
The requirement to decrypt data before processing presents a significant challenge for the current encryption system. While data can be protected by encryption when in motion or at rest, it must be decrypted for use, leaving it susceptible to attacks during processing. This phase allows attackers to exploit the data, underscoring the importance of implementing strong security measures to protect the data in transit. Essential security measures include ensuring secure processing environments, enforcing strict access controls and installing comprehensive monitoring systems. Additionally, the safe disposal of decrypted data after processing is also important to mitigate the risk of data breaches.
From encryption to digital certificates
At the business level, modern encryption encompasses various interconnected components to encrypt communication and data of all forms. This is achieved through the use of digital certificates, which adhere to standards like X.509 or EMV. Today, certificate authorities (CA) sign and issue these certificates, providing a protective shield for different needs. In the realm of encryption solutions, you can count on these digital certificates:
- TLS/SSL (Transport Layer Security/Secure Sockets Layer) certificates are commonly used to secure communication between web browsers and servers. They provide a secure and encrypted connection, ensuring that data transmitted over the internet remains confidential.
- S/MIME (Secure/Multipurpose Internet Mail Extensions) is an email protocol extension providing end-to-end encryption and digital signatures. It allows users to securely send and receive encrypted emails, ensuring that only the intended recipient can access and decrypt the message.
- Code signing is a technique to ensure that software or code has not been tampered with or modified since the developer signed it. It authenticates the source of the code and ensures its integrity, protecting users from potentially harmful or malicious software.
- Document signing involves the use of digital signatures to authenticate the signer’s identity and ensure the document’s integrity. It provides a secure mechanism for electronic documents to be “officially” signed.
These digital certificates are essential in an increasingly interconnected and data-driven world. By employing encryption keys as the foundation of data protection, these digital certificates are based on modern encryption methods and enable the secure transmission, storage and processing of data, maintaining confidentiality and ensuring the integrity of sensitive information.
The importance of advancements in public-key encryption technology
Staying ahead of the game is paramount in a world teeming with hackers and cybercriminals. That’s where advancements in encryption technology come into play, serving as our protection against the ever-growing threats we face in our interconnected society. As adversaries adopt increasingly sophisticated methods, we must actively innovate our encryption technology to safeguard our data and preserve our privacy. By raising the bar with upgraded encryption algorithms and techniques, we fortify the shield between valuable information and those seeking to exploit it. From securing our digital footprints in cloud computing and the Internet of Things (IoT) to fortifying the essence of our mobile communications, the evolution of encryption technology is the key to building trust in our online sphere.
The challenges of encryption in the future
Encryption systems are integral to safeguarding sensitive information in our digital age. However, they face various challenges that jeopardize their efficacy and long-term viability. These challenges include:
1. Advances in technology
Rapid advancements in computing power, quantum computing and artificial intelligence pose significant threats to encryption systems. As technology progresses, so does the ability of malicious actors to exploit vulnerabilities and break traditional encryption algorithms. Encryption methods that are secure today may become obsolete tomorrow, rendering the protected data vulnerable.
2. Quantum computing
Quantum computing has the potential to disrupt current encryption systems. Quantum computers leverage the principles of quantum mechanics to perform complex calculations at an astonishing speed. These computers can solve mathematical problems currently considered computationally infeasible, threatening the security of widely used encryption algorithms such as RSA and ECC (Elliptic Curve Cryptography).
3. Backdoors and weak cryptography
Government agencies sometimes demand the inclusion of backdoors in encryption systems to access encrypted communications for law enforcement purposes. Such backdoors have the potential to be exploited by attackers, compromising the security of the entire system. Additionally, using weak cryptography by specific organizations or individual users further undermines the effectiveness, making it easier for attackers to decrypt the protected data.
4. Key management and human factor
Encryption systems rely on key management to securely distribute and store cryptographic keys. Effectively managing and protecting encryption keys is crucial. However, human error, such as weak passwords, improper storage or accidental disclosure, can compromise the entire encryption system. Moreover, if individuals or organizations fail to implement best practices in key management, it exposes weaknesses that hackers can exploit.
Quantum computing is the main threat to current encryption systems
Decryption without the key is theoretically possible through brute force attacks or other methods. However, it is practically impossible today due to the complexity of breaking encryption algorithms. Encryption algorithms rely on huge prime numbers and complex mathematical functions that are extremely difficult to solve without the key. Yet, emerging technologies like quantum computing could break some existing encryption methods. Quantum computing has the potential to perform complex calculations much faster than conventional computers, potentially damaging encryption keys in a fraction of the time it would take now. As quantum computing evolves, updating encryption algorithms regularly and adopting quantum-safe encryption methods designed to resist quantum computing attacks may become necessary. Researchers are already working on developing quantum-safe encryption methods, and organizations need to be prepared for the possibility of quantum-based attacks and take appropriate measures to safeguard their sensitive data.
The public-key encryption methods of the future
As technology advances, encryption methods are evolving to enhance security and protect sensitive information. The future of encryption will be marked by the integration of advanced technologies that strive to provide unbreakable security, preserve privacy and revolutionize data protection in our digital world. These encryption methods of the future will need to strengthen data protection and safeguard user privacy, promising a new era of secure information exchange. Here are some possible scenarios.
1Quantum cryptography
Quantum cryptography offers a promising solution to encryption by exploiting quantum mechanical properties for cryptographic tasks. Unlike traditional encryption that relies on mathematical algorithms, quantum cryptography utilizes the properties of photons to establish secure communication channels. This method aims to offer an unbreakable encryption system by leveraging the concept of quantum entanglement. For example, quantum key distribution, the most well-known example of quantum cryptography, provides a secure method for exchanging keys between parties, with the advantage of information-theoretic security.
2Homomorphic encryption
Another encryption method of the future will be homomorphic encryption, which allows computations to be performed on encrypted data without the need for decryption. This means that data can remain encrypted while computations are done, resulting in an output identical to what would be obtained from performing the operations on unencrypted data. Homomorphic encryption will find applications in areas such as cloud computing, where data can be securely processed without exposing its contents.
3Blockchain technology
Blockchain technology will continue to evolve and play a significant role in encryption due to its underlying principles of decentralization, immutability and transparency. The distributed nature of blockchain makes it difficult for hackers to tamper with encrypted data, enhancing its security. Additionally, using cryptographic algorithms and hashing techniques within the blockchain provides an added layer of protection for transactions and data. The transparency of blockchain ensures that any attempted manipulation of encrypted data can be easily detected, making it a promising solution for secure and trustworthy encryption in the future.
4Behavioral biometrics
One future development is integrating behavioral biometrics into encryption systems, which analyze unique patterns and behaviors exhibited by individuals, such as typing rhythm, mouse movement, voice patterns and gait. These traits enhance authentication and encryption, making it more robust and difficult to bypass. This integration provides accurate and personalized security, detecting unauthorized access. Encryption systems ensure that only authorized individuals can access sensitive data and communication channels by capturing and analyzing these behavioral patterns. This technology adds a layer of security, identifying anomalies in behavior patterns and triggering additional measures or denying access if an attacker obtains login credentials.
Make public-key encryption harder, faster and stronger
The problems surrounding current encryption systems underscore the need for proactive measures in safeguarding sensitive data. As we navigate the present, it is equally important to keep an eye on the future and the potential dangers that may arise. The looming threat of quantum technology necessitates a proactive approach to data security. By taking action now, organizations can position themselves on a more secure footing and play a part in shaping the future of encryption.
Stay updated on the most up-to-date encryption technologies for your business and explore digital certificates that provide robust data security so your organization remains protected in the ever-changing landscape of data encryption.