Document signing | How it works

In an opaque system designed for anonymity, digital signatures deliver a reliable method to verify identity and authenticate documents, giving us a much needed framework to sign and share legally valid documents in digital form. This article takes a look at what digital signatures do and how they work.
Published by

Natalie Berrisford
Date
The conclusion of personal and commercial interactions is built on trust. To indicate consent to an agreement or approval of content and create a mutually binding understanding or obligation, we use socially and legally established norms such as handshakes or signatures. This is based on our confidence in the identity of the party that we are conducting business with – we trust that the other person or party is, in fact, who they say they are.
In the physical world, the business of identification is made easier by the fact that we can physically hear, see and interact with our counterparts. Nevertheless, the verification of a person’s identity often requires the inspection of documents like identity cards or passports. Other means of verification, such as fingerprints or voice, facial and retina recognition, have also become common. Despite all of these established measures, the potential for counterfeiting and fraud still exists.
Identity is key
Once the issue of identity has been clarified, so-called wet signatures, actual ink on paper, can be used to complete agreements between parties (e.g. contracts), authorize or approve (e.g. initials on workflows) or authenticate official documents (e.g. birth certificates). Such documents almost always include information like names or initials, official job titles, time and place.
They very often include physical features that are designed to prevent manipulation and to allow others to check the validity of the document. These features include, amongst others, stamps, seals, watermarks and the use of special papers and printing inks.
New system. New rules.
But this conventional, physical paper-based system is changing – and so are the rules. With the rapid and ongoing corporate shift to doing business online, users and companies are looking for solutions to perform the same legal activities on digital documents. However, the question of checking and providing identity and validity remains central.
In this respect, the structure of the internet does not inherently allow for transparency. Quite the opposite is true – the system is effectively geared towards providing and protecting user anonymity. And this is exactly where digital signatures, which bind proof of the identity of the signatory to the signature field using cryptography, step into the limelight. In this article, we’ll take a closer look at what exactly digital signatures are, how they work and what they look like.
Electronic or digital – it’s the same thing, right?
Although the terms “electronic signature” and “digital signature” are often used synonymously, they do not not refer to the same type of signature. More specifically, a digital signature falls under the broader category of electronic signatures.
Let’s take a closer look:
An electronic signature or e-signature is the broad term used to describe any kind of data in digital form that is attached to other data with the purpose of functioning as a signature. It can take many forms. It could be as simple as an image of a signature included in a PDF file or merely a typed name at the end of a document or email. These kinds of basic electronic signatures do not require the signatory to provide any verification of identity. They are based on trust on the part of the individual accepting the document as agreement.
Depending on the jurisdiction and use case, basic electronic signatures can be a legally viable way to complete an agreement. However, for many sensitive or high value use cases, they may not be considered appropriate to mitigate potential legal or commercial risks.
A digital signature is a specific type of electronic signature that uses advanced cryptographic techniques for added security and verification. They use a hashing algorithm to attach verification of identity to the signature while providing data about the document’s integrity, creating a unique digital fingerprint of the document which is encrypted and attached to the digital signature certificate.
This allows the recipient to make sure that the document has not been manipulated and to verify the signatory’s identity. These types of digital signing certificates are issued by established certificate authorities (like DigiCert) after a thorough validation process.
Good to know
As regulations differ between countries and industries, it’s important to check which type of digital signature meets the relevant requirements for the region and the specific use case.
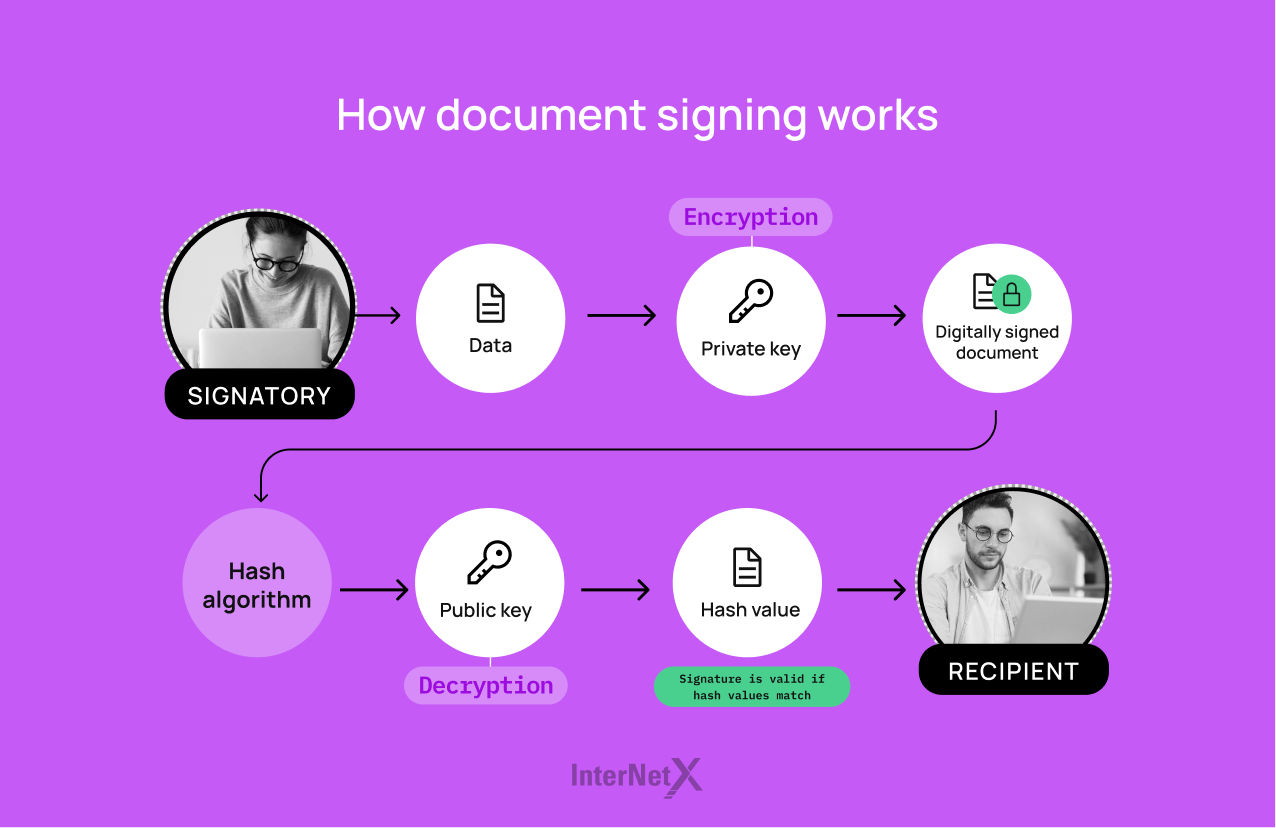
How document signing works
- The signatory creates a digital signature using a private key that is generated by a cryptographic algorithm.
- The document is then hashed using a cryptographic algorithm which creates a unique digital fingerprint of the document’s content.
- A digital signature block is then created with the digital signature along with the hashed content.
- The digital signature block is attached to the original document and it is then ready to be sent to the recipient.
- To decrypt the signature block and verify the authenticity of the digital signature, the recipient uses the signatory’s public key.
- The hash value of the original document contained in the decrypted digital signature is then compared to a new hash value in order to verify that the document has not been manipulated. If the hash values match, the recipient can be assured that the signature is valid and the document has not been altered.
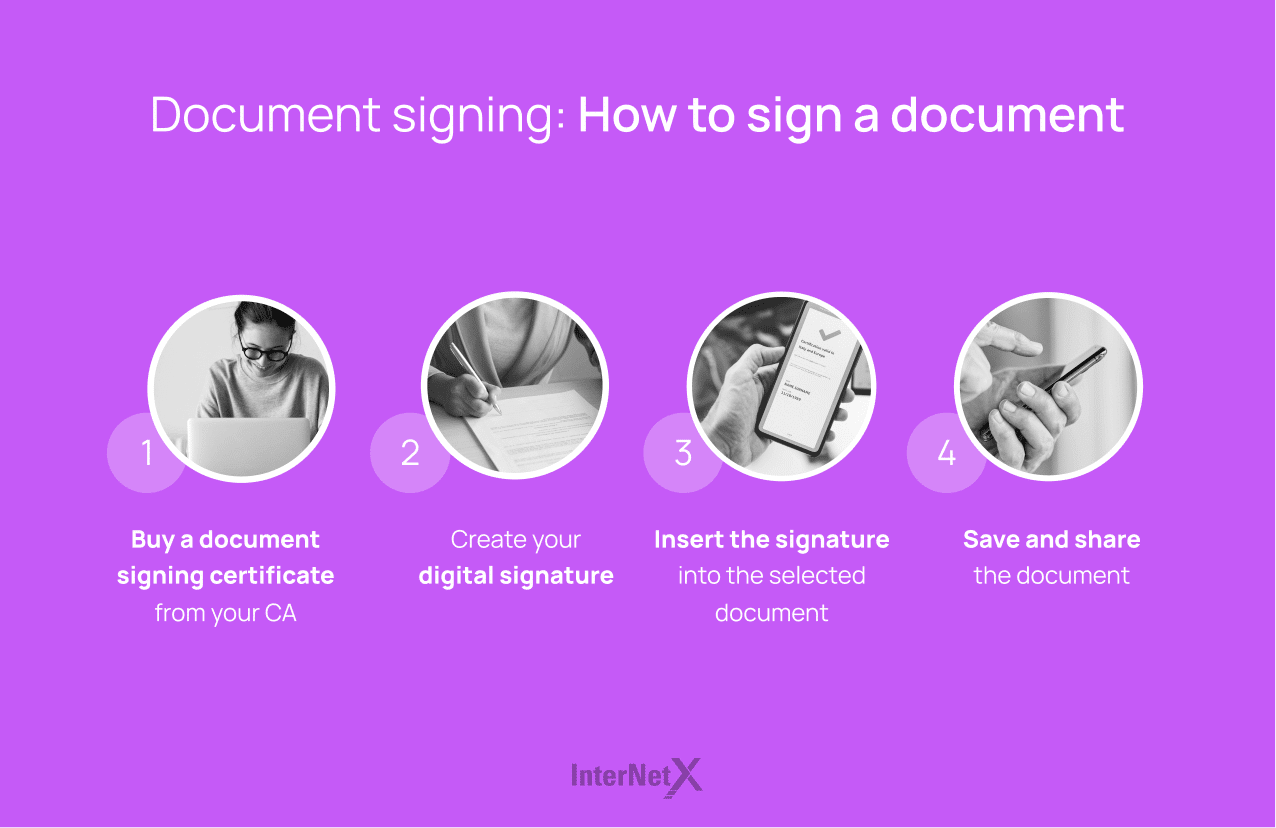
How to sign a document
The first step is to buy the appropriate document signing certificate from a trusted provider. Each document signatory must have their own digital certificate, and, depending on the use case, a specific type of digital signature may be required to form a valid agreement in that jurisdiction.
The certificate will either be delivered digitally as a download, such as with a digital ID, or sent to you on a qualified hardware token (USB). Depending on whether you are signing a document locally on a computer or using a signature workflow service, there may be differences in how you apply a digital signature.
- Signature workflow service
When you open the document to sign, you will most likely be prompted to apply your signature in a specific digital signature field.
- Local signature
If you are signing locally on your desktop, you may need to choose the location where you want to place your signature by inserting a digital signature field into the document. Then, click in the digital signature field in the document and you are asked to authenticate your identity and authorize the use of your unique digital certificate to sign the document.
Some signature workflow solutions may create a separate file with the digital signature that can be used to verify the authenticity of the signed document. Or, when opening a signed document in Adobe® Acrobat Reader, the signature panel can be used to verify the chain of trust to confirm that the document and associated digital signatures have not been tampered with and are valid.
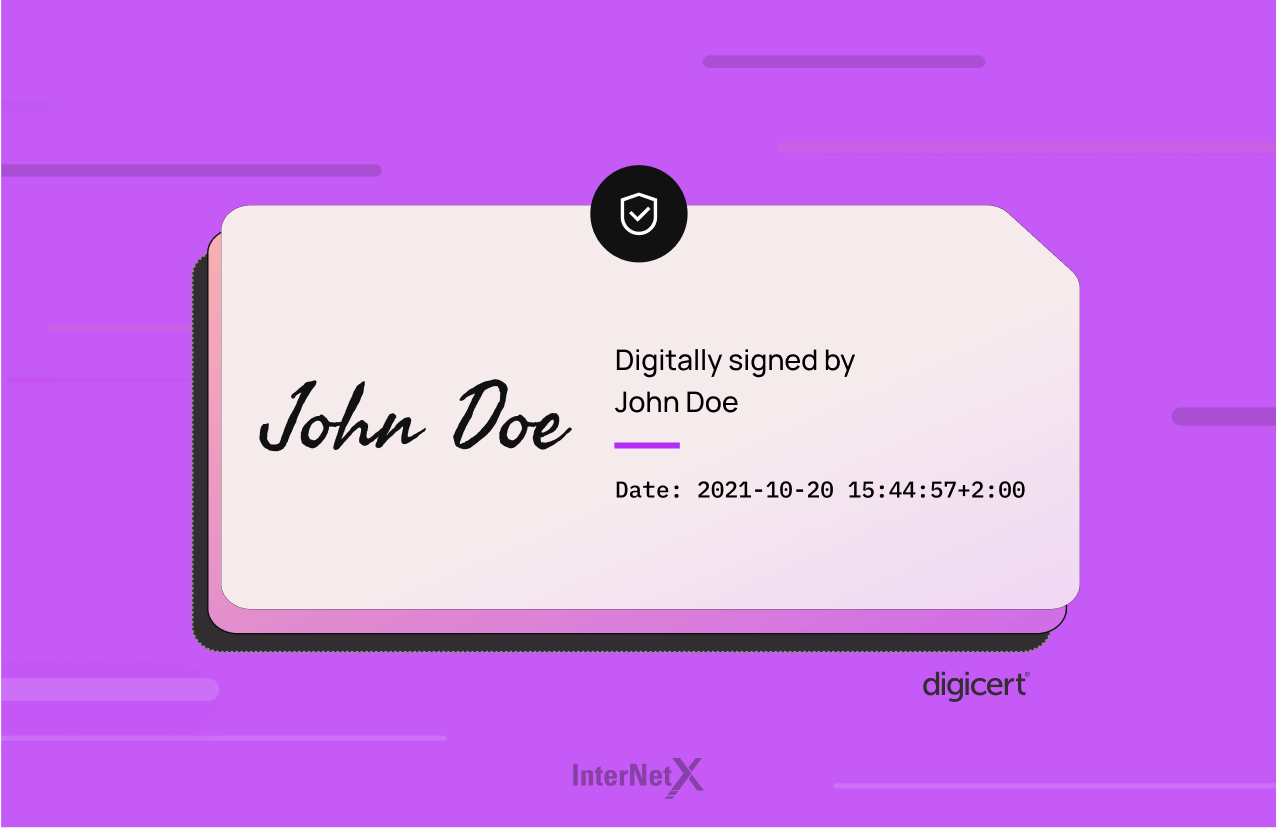
What does a digital signature look like?
The appearance of a digital signature varies depending on the software used to create and verify it. Some signature workflow solutions may display the signature with a check mark or a green banner indicating that the chain of trust is intact.
In documents, a digital signature most often looks like a block of text or an image that contains information about the signatory, such as their name, email address and possibly their position. It will usually also include a timestamp that indicates when the document was signed and may also include other information, such as the certificate issuer and the certificate’s serial number.
In addition to this, the digital signature also includes a unique cryptographic code that can be used to validate the authenticity and integrity of the signature. Detailed information relevant to the signatory’s unique digital certificate can usually be accessed by clicking directly on the signature itself or via menu options in the application.
This will display all relevant information about the certificate, the issuing certificate authority, the signatory and the integrity of the document along with the document’s audit trail.
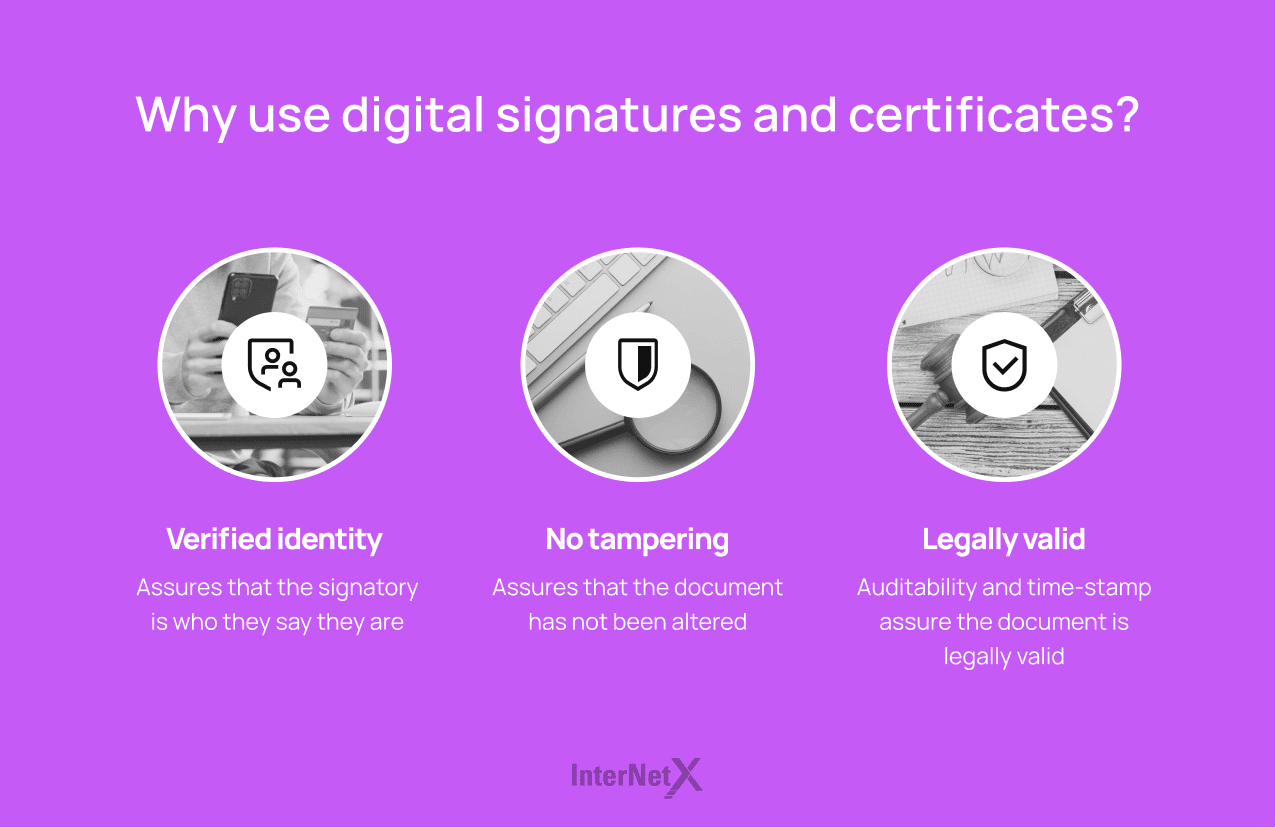
Why use digital signatures and certificates for your documents?
- Digital signatures are fast becoming part of the standard procedure for sharing documents in digital form. As industries and regulations are driven towards digitization, solutions for signing digital documents are rapidly gaining in importance.
- Digital signatures can provide high assurance of the signatory’s identity, the document’s integrity.
- Digital signatures provide a basis for strong legal evidence that a specific individual signed a specific document, and it has not been tampered with since the signature was applied.
Take a look at the full spectrum of encryption products and find the perfect solution for your business and use case.