Elliptic curve cryptography (ECC)

Encryption is fundamental for internet security and elliptic curve cryptography (ECC) will become the next standard in the industry. Find out why and keep up to date with the latest security improvements.
Published by

Simone Catania
Date
From internet surfing to data transfers, banking transactions and messaging apps, the web is an ocean of sensitive or personal data information. Security experts have been working hard to create technology capable of thwarting hackers. Computer science has adopted encryption to secure information by mathematically encoding it. Behind its functioning are algorithms that developed over a thousand years of progress.
So why do we need encryption? The immensely widespread and ever-expanding use of the global internet requires us to adopt very secure solutions. While RSA encryption, based on private and public keys, has been the standard for decades, things are now moving on to a new, high-performance standard that is able to face even quantum computing scenarios.
Today, elliptic curve cryptography (ECC) is regarded as one of the most robust types of encryption and has become a valuable ally for cybersecurity. We invite you to read this article for a more detailed introduction to ECC encryption and to discover why it is set to become the next internet standard in its field.
What is encryption?
Nowadays, encryption is the standard measure to protect communications in the digital ecosystem. Its extensive protective shield spans from HTTPS connections to securing information transmitted in data centers.
Encryption belongs to the ancient field of cryptography and is a process for encoding information. It has been used for centuries to convert the original message into unintelligible ciphertext that only the authorized and intended recipients can decipher. Both then and now, the aim was to avoid unauthorized parties from accessing critical information or communications.
Symmetric encryption vs asymmetric encryption
We can distinguish between two main widespread forms of encryption today, namely symmetric and asymmetric encryption. The main difference lies in whether the same key is used for encryption and decryption.
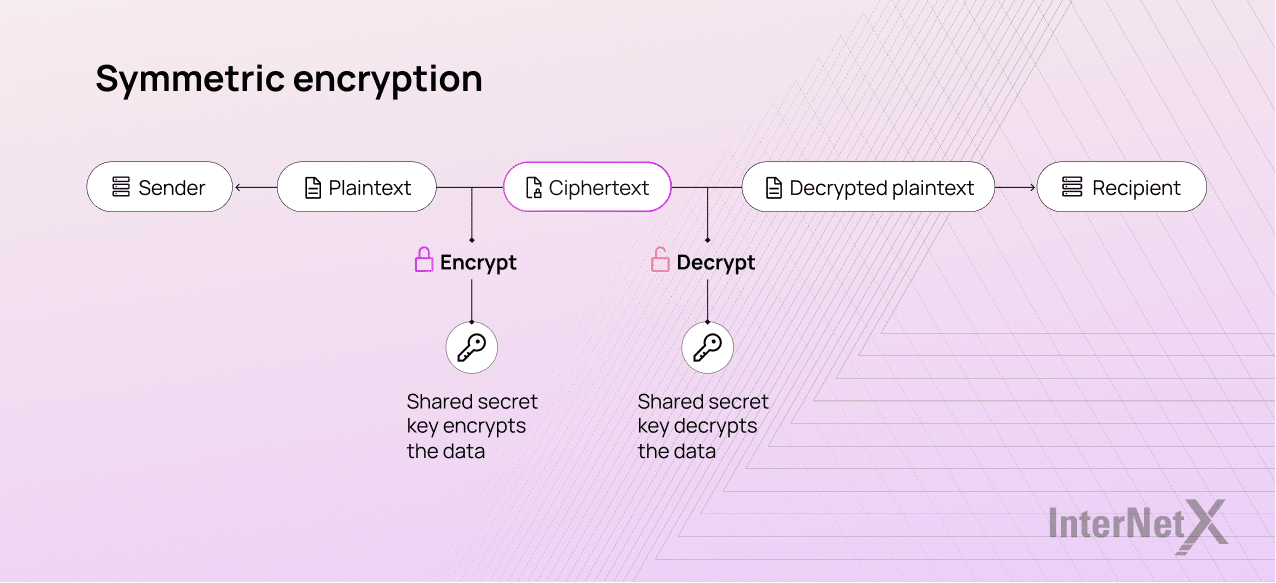
Symmetric encryption
When the sender and the recipient share only one single key, we speak of symmetric key cryptography. The single key is used to both hide and unlock the message. Compared to other types of encryption, it is quick and easy.
Well-known examples of symmetric encryption include:
- Data Encryption Standard (DES)
- Triple Data Encryption Standard (Triple DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- TLS/SSL protocol
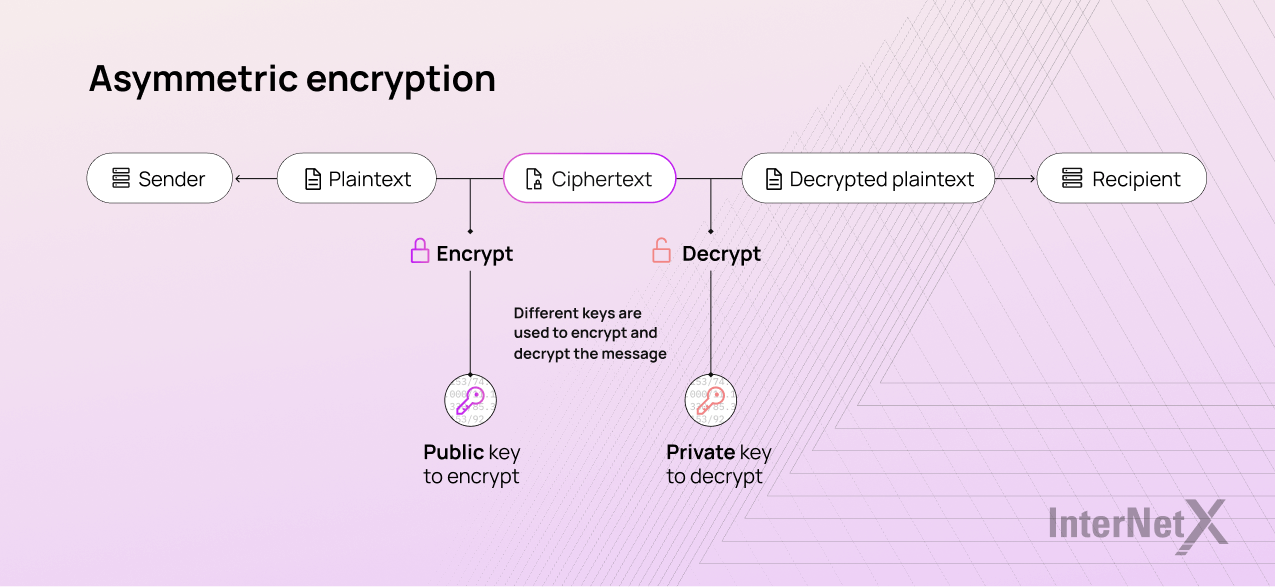
Asymmetric encryption
Asymmetric algorithms use two interdependent keys, a public and a private key, one to encrypt data and one to decrypt it. The recipient knows both keys, the private and the public one. He should never share the private key that he needs for decryption. The public key is used by the sender to encrypt the message. One of the most common uses of asymmetric cryptography is to digitally sign a certificate in order to verify the authenticity of a document or the integrity of a message.
Examples of asymmetric encryption include:
- Rivest Shamir Adleman (RSA)
- Digital Signature Standard (DSS), which incorporates the Digital Signature
- Algorithm (DSA)
- Elliptic curve cryptography (ECC)
- the Diffie-Hellman exchange method
- TLS/SSL protocol
Brief add-on about TLS/SSL encryption
Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are encryption methods used for protecting data over the internet or a computer network. Having a TLS/SSL certificate on your domain has become the standard for most web browsers or servers. These two types of encryption can follow the symmetric and asymmetric models with different goals to protect the internet. While symmetric encryption protects data exchange within a session, asymmetric encryption establishes secure communication between the client and server.
Elliptic curve cryptography: future-proof security
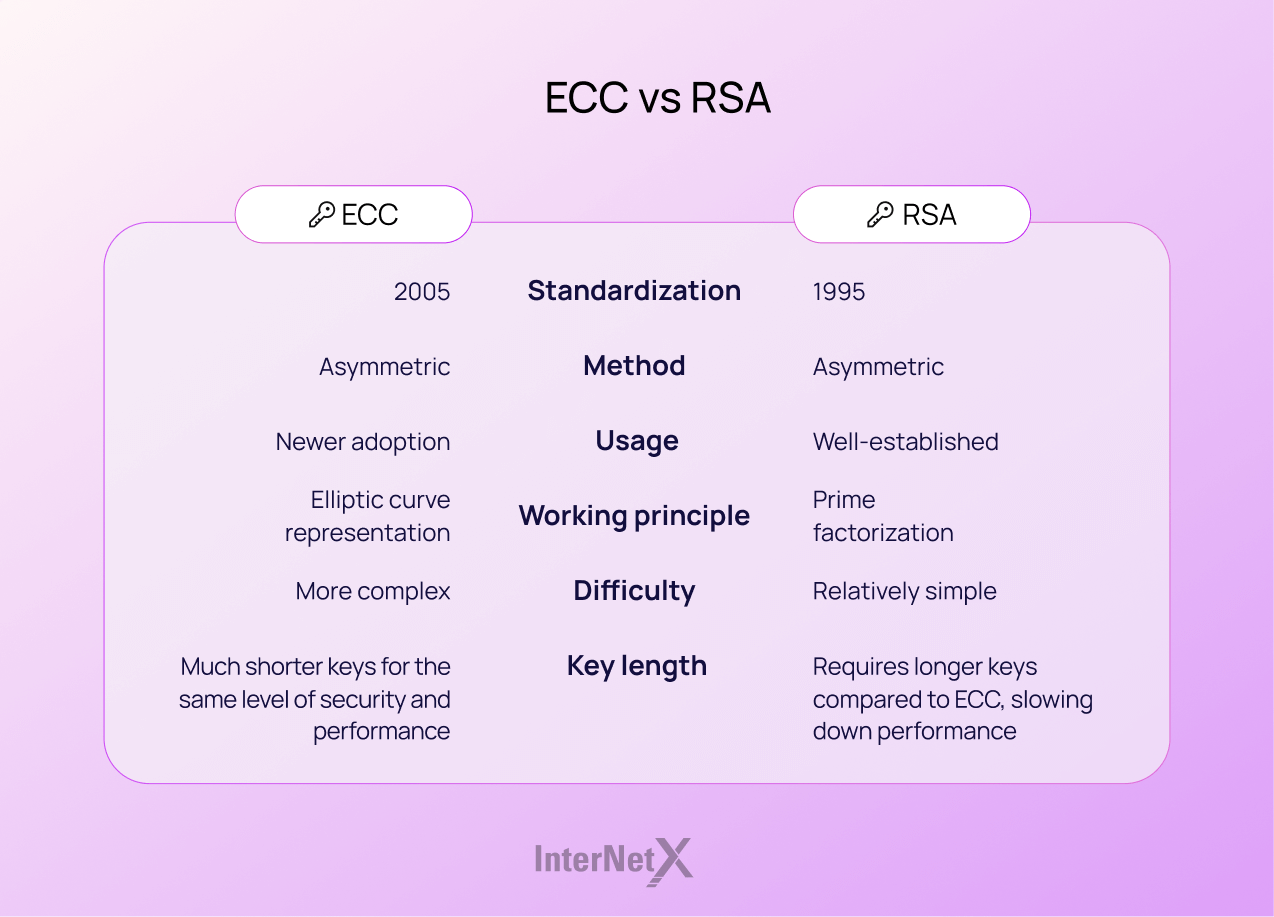
The concept of elliptic curve cryptography (ECC) is not new, at least in mathematics. It was proposed in the mid ’80s by Victor Miller of IBM and Neal Koblitz of the University of Washington.
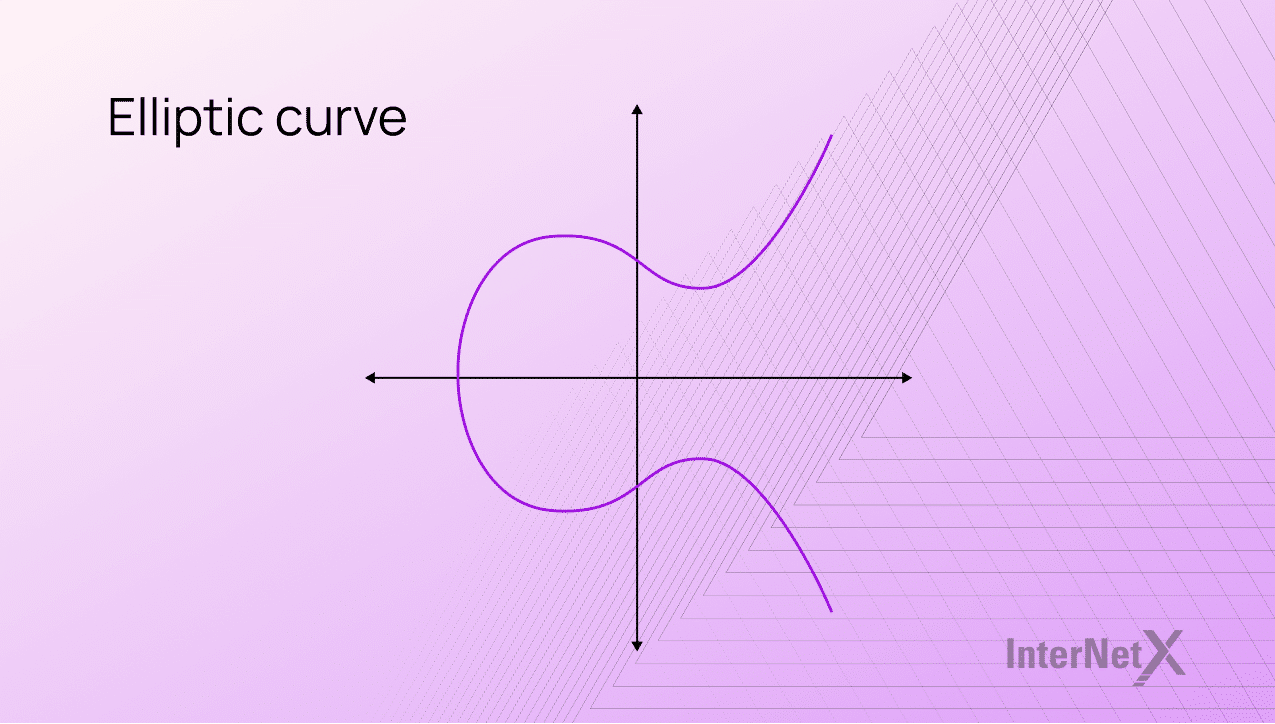
Elliptic curve encryption algorithms started enjoying widespread use around 2004-2005. The use of ECC in computer science has recently established itself as a more robust alternative to public-key systems like RSA, DSA and Hellmann. One of the most known uses is probably the Elliptic Curve Digital Signature Algorithm (ECDSA). ECC is a form of public-key cryptography or asymmetric encryption, freely distributed with a private key and a public one.
ECC finds a distinct logarithm within a random elliptic curve, in contrast to RSA, which uses large logarithms as security measures. The greater the elliptical curve, the greater the safety. Using a random formula improves the strength of the encryption, while a smaller logarithm increases the performance of digital certificates.
The Federal Information Processing Standard (FIPS) certified the ECC standard with the further approval of the National Security Agency. Adopting this strong cryptography will help us migrate to higher security strengths.
What is an ECDSA?
ECC has many groups of algorithms for digital signature, encryption and key agreement. The most well-known signature scheme that uses elliptic curves is the Elliptic Curve Digital Signature Algorithm (ECDSA). It is an alternative encryption system to the classic Digital Signature Algorithm (DSA) system using elliptic curves. It was proposed for the first time by Scott Vanstone.
ECDSA is increasingly used to encrypt software and generate Bitcoin, blockchain keys and sign cryptocurrency transactions. Thanks to the shorter key lengths and its high efficiency, it has become quite popular.
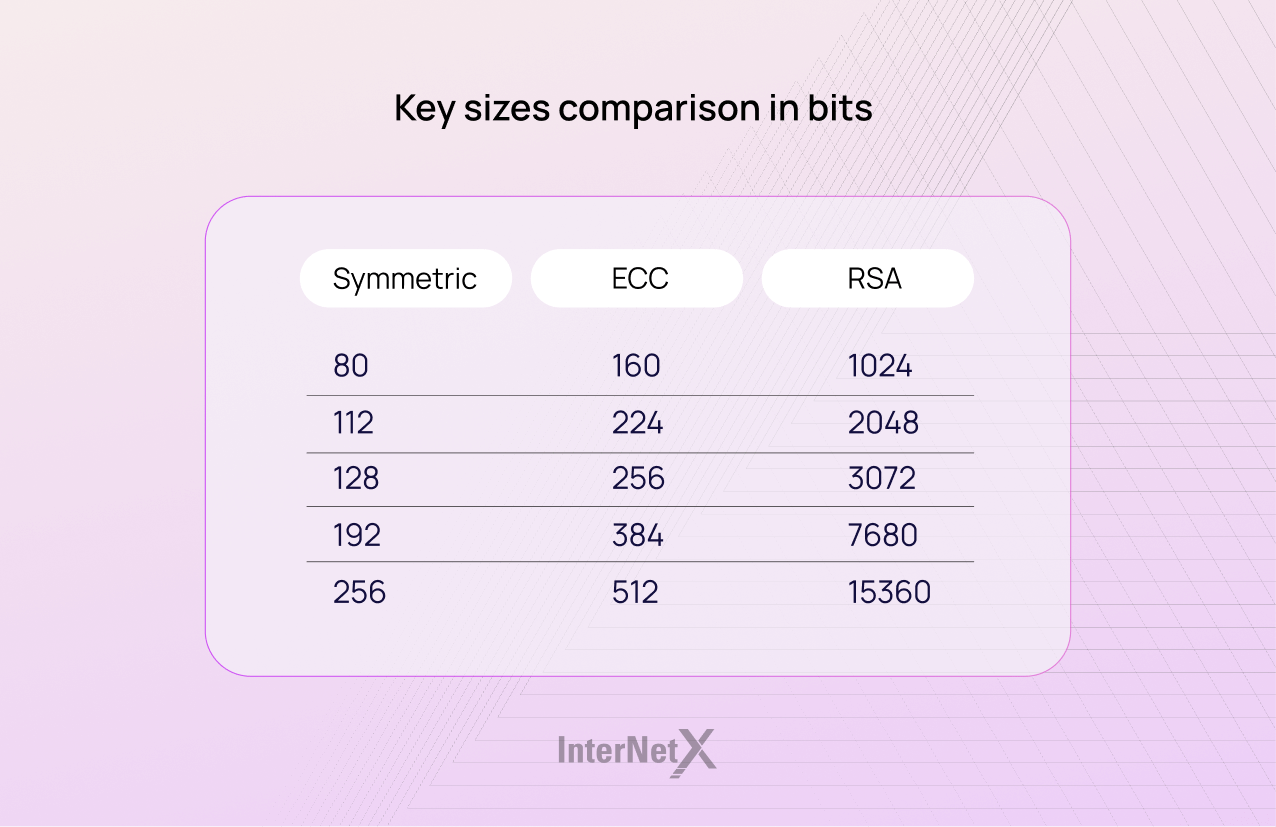
As is commonplace for elliptic curve cryptography, the bit size of the public key needed by ECDSA is approximately twice the size of the security layer in bits. Therefore, if the security level is 100 bits, then a key size of 200 bits is required. The shortest bit length can be 1,024 or even 3,072 bits. This results in faster algorithms and improves performance.
This is why ECC is crucial for the internet
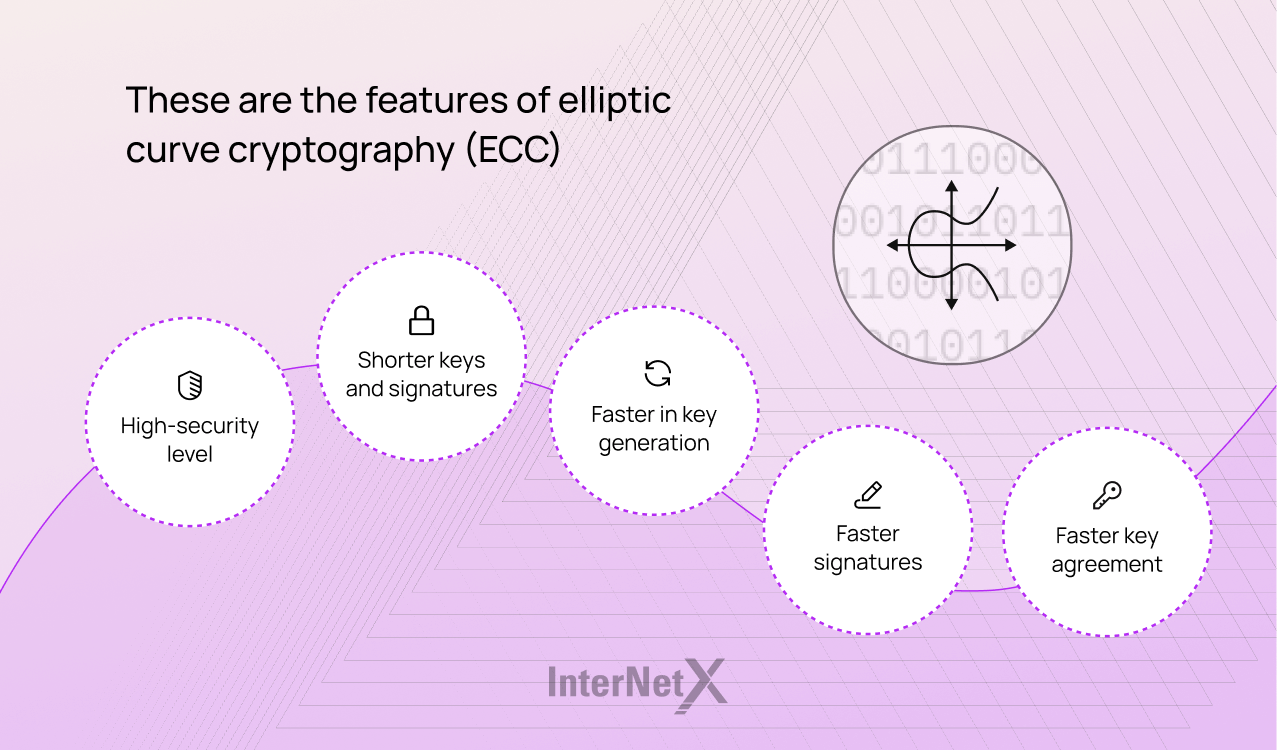
Despite being relatively new, ECC has been used successfully over the past few years, proving to be a reliable and potent solution. This new encryption method has the right features for the digital world with its extensive data volume exchange. It can guarantee a higher level of security, better performance and shorter keys for increased speed.
The shorter keys require less computing power, which means secure and faster connections. For example, a 256-bit ECC key provides the same security level as a 3072-bit RSA key. This element is particularly crucial in a world where users predominantly browse the web with mobile devices such as smartphones and tablets.
These are the advantages of ECC digital certificates
Digital certificates with ECC have more advantages. They are generally lighter, faster and more secure than RSA. Keys in RSA are massive, almost unwieldy. The current standard is 2048 bit, though some go up to 4096 bits. Let’s take a detailed look at the advantages of ECC.
- Stronger keys
ECC uses a smaller algorithm to generate exponentially stronger keys. - Higher security
The elliptic curve-based systems are tougher than RSA and can withstand quantum computing. - Increased performance
A smaller algorithm means less data is verified between the server and the client, which results in increased network performance. This comes in especially handy for websites with a high level of traffic. - Better scalability
ECC requires less CPU and goes easier on resources. It allows more simultaneous TLS/SSL connections and faster page loading. - Compliant and accepted
ECC is supported by the NSA and is compliant with the NIST 800-131A guidelines.
ECC has downsides as well
Although ECC provides an excellent alternative to the traditional public-key scheme, it has some disadvantages compared with RSA encryption.
The ECC algorithm is relatively new, which opens it up to potential unknown weaknesses. It is more complex and could be challenging to set up securely. This increases the likelihood of implementation errors, reducing the algorithm’s security. Understanding the EC-based protocol requires a congruous wealth of algebraic and geometric skills!
What is the security level offered by ECC? Ways and means to attack ECC and exploit its vulnerabilities do exist. For example, side-channel or twist-security attacks can invalidate the safety of private keys. Proper countermeasures, parameter validation and appropriate curve choices can mitigate these threats. Although not 100% secure, ECC still remains an extremely effective and highly secure method.
Do you want to start using ECC certificates?
Elliptic curve encryption is the most advanced encryption system available. TSL/SSL certificates with ECC are ideal to scale up your business. They perform at their best for scenarios in which the server load is critical and website or app users are compatible with ECC keys.
At InterNetX, you can opt for this technology for all your web, mobile and desktop applications services.
More about digital certificate with ECC