Domain shadowing | Prevent, combat, secure

Warning: Domain shadowing is an emerging threat. Implementing all best practices to prevent attacks and secure your domains is imperative.
Published by

Simone Catania
Date
Domain shadowing is a growing threat that demands your attention. In a web scan conducted between April and June 2022, the threat analysts from Unit 42 at Palo Alto Networks uncovered 12,197 instances of domain shadowing, suggesting that this phenomenon may be more widespread than initially believed. For a long time, domain names have frequently been exploited for malicious online activities. Previously, criminals primarily created new domains for their attacks. But, since existing systems can now prevent harmful domains from being registered, hackers have adopted new procedures. Domain shadowing involves taking control of legitimate domains and creating malicious subdomains under them. This tactic challenges countermeasures, as subdomains typically enjoy the authority of the primary domain. So, how can you prevent, mitigate and secure your domain against domain shadowing?
Join us as we delve into the topic of domain shadowing, explore the impact it has on companies and organizations and learn how to effectively prevent and detect such attacks.
Successful business = safe domains
Securing domain names is vital for your business’s success in today’s competitive market. A safe online presence helps establish customer trust, protect sensitive information and ensure seamless operations. Incidents connected to domain names and DNS servers can result in data breaches, service interruptions as well as damage to your company’s reputation. To counter these threats, your business must prioritize DNS security by staying informed about emerging risks, including domain shadowing, and implementing effective countermeasures to safeguard the integrity of your domains.
A successful business will recognize the importance of protecting its domains to maintain a strong online presence.
What is domain shadowing?
Domain shadowing is a technique that cybercriminals use to secretly create and control subdomains under a legitimate domain without the owner’s knowledge or consent. This tactic has become a significant concern for DNS experts and brand managers.
By gaining unauthorized access to a domain’s DNS settings or domain registration accounts, often via phishing or credential stuffing, hackers can create a network of malicious subdomains. This approach allows threat actors to bypass traditional security measures, hinder domain takedown processes and make it difficult for security researchers to track their infrastructure.
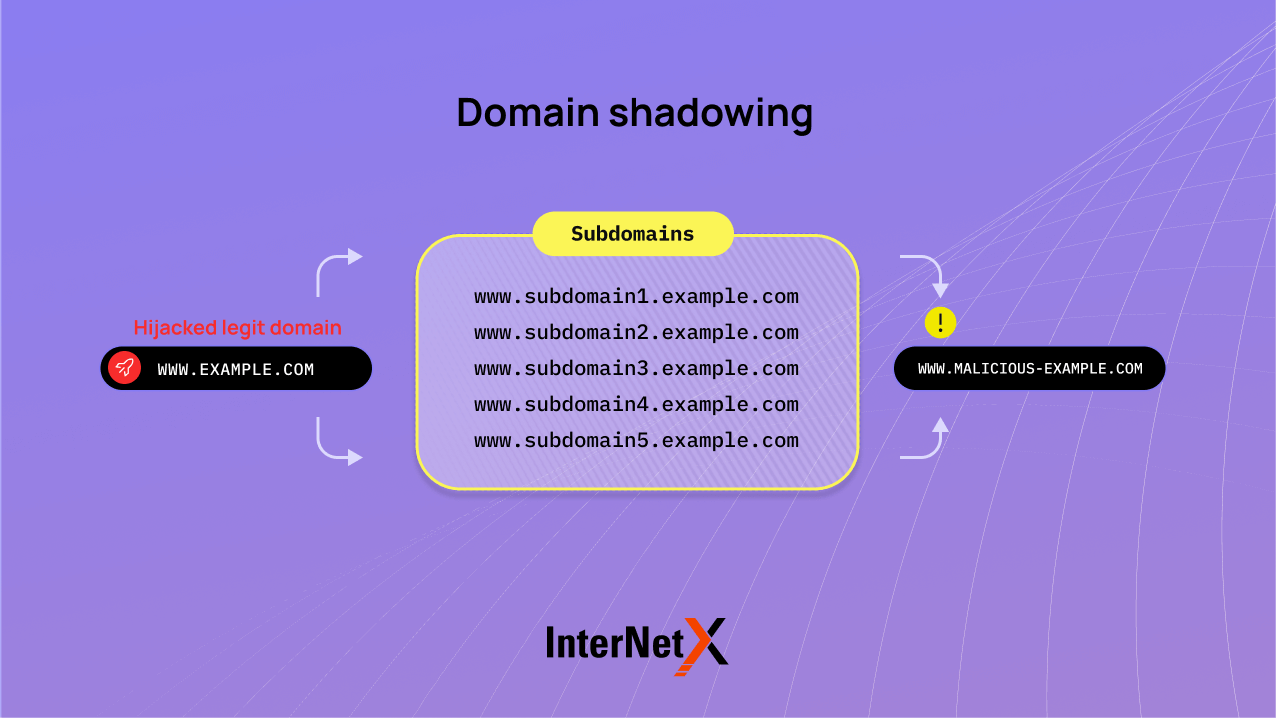
Hackers can use the shadowed domains for harmful purposes like running phishing websites, spreading malware or managing botnet command and control infrastructure. One main goal is to evade detection and extend the lifespan of malicious campaigns by exploiting the trust and reputation associated with the compromised domain.
Users may not realize they are on a fake site since the URL bar displays the main domain with a reliable reputation.
A retrospective look into domain shadowing
According to an analysis conducted by the Cisco Talos Intelligence Group, the first behavioral evidence of domain shadowing traces back to September 2011. It involved a group of related domains and many subdomains, constructed with random strings and active for less than a day.
Until mid-2014, sporadic subdomain usage was observed, with a significant campaign in May 2014 involving a browser lock campaign and police and alert police subdomains forwarding to compromised systems and providing payment details. After that, Talos observed a growing number of domains linked to various domain accounts being used maliciously. The first large-scale campaign focused on the Angler Exploit Kit, a toolkit designed to exploit vulnerabilities in various software applications and allow cybercriminals to distribute malware and gain unauthorized access to affected systems. Since then, the scope and amount of domain shadowing activity have undergone significant growth. From December 2014 onwards, domain shadowing has expanded to become an increasingly real and global threat. The fast-paced process of digitization has exacerbated this issue.
Real-world scenarios of domain shadowing threats
In 2017, a task force comprising IT security firms and registrars took down tens of thousands of unauthorized subdomains tied to the RIG Exploit Kit, a cybercrime tool. Upon gaining access to various accounts, the attackers created subdomains that hosted the exploit kit, furthering the attackers’ malicious actions.
In 2022, hackers took over a subdomain of Wired.com for several months and replaced its content with online casino advertisements. The hackers may have hijacked DNS records, hosting their subdomains for malicious use without modifying the legitimate DNS entries. The subdomain looked authentic and ranked well in searches because of Wired’s credibility and high domain authority.
Why is domain shadowing hard to detect?
Domain shadowing poses a significant challenge for cybersecurity professionals due to its elusive nature. There there are a few reasons for that:
- Access to your web server is not required for the hackers to launch a domain shadowing attack.
- The malicious subdomains are hosted on another server and you won’t find them anywhere.
- Using these “genuine” domains makes it challenging for security systems to identify and flag suspicious activities as they often blend in seamlessly with normal web traffic.
- Attackers frequently employ automated tools to generate a large number of subdomains, further obscuring their malicious activities.
- Rapid creation and deletion of these subdomains enable cybercriminals to evade detection, as they can quickly switch to new subdomains once the previous ones are identified or blacklisted.
- Hackers often rely on domain shadowing by using compromised access credentials, which they can obtain through various means, such as phishing, credential stuffing or social engineering attacks.
This constant subdomain rotation, combined with the abuse of legitimate domains, significantly complicates detecting and preventing domain shadowing. The fact that the attackers operate within the boundaries of an authorized account makes it even more challenging to detect. Consequently, in order to combat the elusive threat of domain shadowing effectively, organizations must adopt a multi-layered security approach, including monitoring domain registration activities, enhancing user awareness and deploying advanced threat detection solutions.
The threats posed by domain shadowing
Domain shadowing poses significant cybersecurity risks. By exploiting the trust that users and security systems place in legitimate domains, attackers can bypass security measures and deceive users into interacting with malicious content. Using multiple subdomains makes it difficult to detect and block harmful actions, as it allows the attackers to blend in with legitimate traffic. This enables them to maintain a continuous presence within their target networks, making detecting and eliminating threats harder. Domain shadowing is most often used for hosting phishing sites, distributing malware or launching other cyberattacks, all while hiding under the veil of a legitimate domain. Additionally, it can result in severe consequences for the domain holder and brand managers, including reputational damage, loss of customer trust and potential legal implications.
Domain shadowing threats for…
- DNS experts: Difficulty tracking and mitigating malicious activities, increased workload and potential damage to DNS infrastructure.
- Website owners: Loss of website traffic, reputation damage, potential data breaches and financial losses due to malicious activities.
- Brand managers: Negative impact on brand image, loss of customer trust, potential legal implications and increased efforts in monitoring and protecting brand assets.
How domain shadowing exploits the DNS
Domain shadowing is closely related to other DNS-based attacks, such as DNS hijacking and cache poisoning. However, this technique is unique because it leverages the trust users place in the primary domain, making it more difficult to detect and mitigate. Attackers employ various methods to carry out domain shadowing attacks:
- Phishing and social engineering: Attackers may use phishing emails or other social engineering tactics to trick domain holders into revealing their login credentials.
- Exploiting vulnerabilities: Vulnerabilities in content management systems (CMS) or web applications can be exploited to gain unauthorized access to DNS settings.
- Brute force attacks: Attackers may use automated tools to attempt multiple login combinations in the hope of gaining access to domain registrar accounts.
These are the techniques behind domain shadowing
Several techniques used in domain shadowing enable attackers to exploit vulnerabilities in the DNS infrastructure and maintain a stealthy presence within a compromised domain. Some of these techniques include:
Phishing and theft of credentials
Attackers often use phishing emails or other social engineering techniques to trick domain administrators into revealing their login credentials. Once the attacker can access the domain account, they can create and manage subdomains within the compromised domain.
Automated subdomain creation
Attackers may sometimes use automated scripts or tools to create many subdomains under the compromised domain. This makes it difficult for security systems to identify and block malicious subdomains, as they are hidden within the legitimate domain infrastructure.
Domain generation algorithms (DGAs)
In some cases, attackers may use DGAs to generate many seemingly random subdomains. These algorithms make it difficult for security systems to predict or identify malicious subdomains, as they appear unrelated to the compromised domain.
DNS manipulation
Attackers may manipulate a domain’s DNS records by compromising the domain registrar or exploiting vulnerabilities in the DNS infrastructure. This allows them to redirect traffic to their servers and create malicious subdomains.
Malware injection
Cybercriminals may inject malware into a legitimate website, often through compromised plugins or themes. The malware can open doors, allowing hackers to access credentials which can then be used to manipulate DNS settings and create malicious subdomains.
By employing these techniques, domain shadowing enables cybercriminals to host and distribute malicious content while evading detection and maintaining a foothold within the target domain.
Fast flux vs. domain shadowing
Fast flux is often compared to domain shadowing because of their similarities. Both evade detection and blocking techniques by changing IP addresses associated with domains. But, they differ notably with regard to their implementation and manipulation of DNS records.
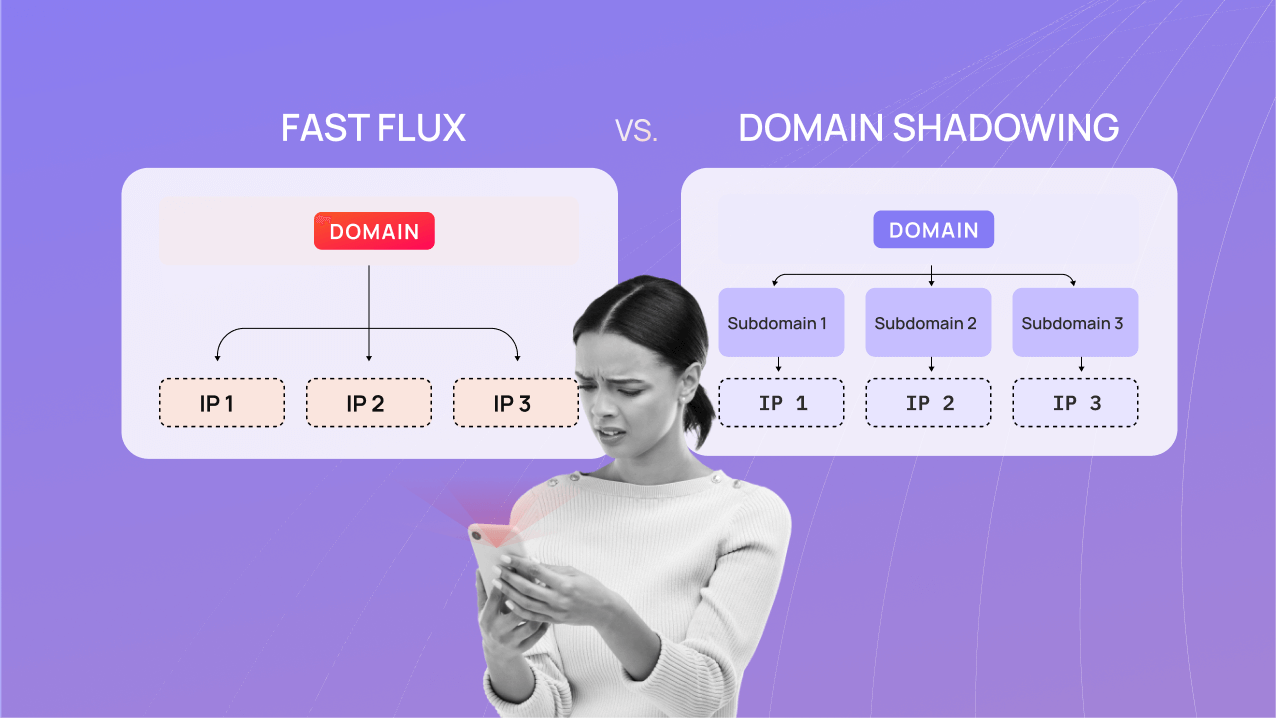
Fast flux changes the IP address associated with a domain. It does this by quickly rotating a single domain or DNS entry to an extensive list of IP addresses, making it difficult for security systems to keep up with the changing IPs. Contrarily, domain shadowing involves the rotation of subdomains associated with a single domain. Instead of changing the IP addresses, domain shadowing creates multiple subdomains under a legitimate domain, making it difficult for security systems to detect and block malicious activities.
Fast flux vs. domain shadowing: Key differences
Fast flux
- Rotates a single domain or DNS entry to an extensive list of IP addresses
- Hides the actual location of malicious servers
- Maintains availability of malicious servers
Domain shadowing
- Rotates subdomains associated with a single domain
- Subdomains can point to a single IP or a small group of IP addresses
- Often used in phishing and malware campaigns to evade security researchers
Strategies for identifying and mitigating domain shadowing
Yes, detecting domain shadowing can be challenging. However, best practices and techniques are available to help domain holders and administrators identify potential domain shadowing activities.
To effectively detect and prevent domain shadowing, organizations should adopt the following strategies:
1 Monitor DNS records and traffic
Monitoring DNS records and traffic can help identify unusual changes or suspicious subdomains. Tools like DNSQuerySniffer and DNSViz can be helpful in this.
2 Domain reputation services
Services such as Google Safe Browsing and VirusTotal can help identify whether a domain or subdomain has been flagged for hosting malicious content, indicating potential domain shadowing.
3 Good password hygiene
Practice good password hygiene by using strong, unique passwords for each account and updating them regularly. Consider using a password manager to generate and store complex passwords securely.
4 Strong authentication and login monitoring
Enable multi-factor authentication (MFA) wherever possible to add an extra layer of security. For example our DomainSafe. This requires users to provide two or more forms of identification, such as a password and a verification code sent to a mobile device.
5 Restrict access to administrators only
Limit the number of users with administrative privileges to reduce the potential for unauthorized access. Ensure that only those who need administrative access have it and regularly review and update permissions.
6 IP restrictions
Ensure that only IP addresses previously defined by the customer can access your web interfaces and APIs. In AutoDNS, you can add an extra layer of security by limiting access to authorized users only.
7 Monitor DNS settings
Consistently and proactively review and monitor DNS settings for any unauthorized changes, suspicious subdomain activity or potential security threats in order to ensure the integrity of your domain.
8 Educate users
Provide regular training and awareness programs to educate users about DNS security, the latest security threats, phishing scams and best practices for online safety. Encourage users to report suspicious emails or activity to the IT team.
9 Login monitoring
Implement active login monitoring to prevent brute force attacks and suspend accounts or IPs with excessive failed attempts. Notify customers of suspicious logins from new devices or unknown locations for enhanced security awareness.
10 Use DNS security tools
Implement DNS security tools like DNSSEC (Domain Name System Security Extensions) to protect against DNS spoofing and cache poisoning attacks. DNSSEC adds a layer of security by digitally signing DNS data to ensure its authenticity. However, DNSSEC alone does not prevent the malicious creation of subdomains.
11 Apply a registry lock
Enable a registry lock for your domain to prevent unauthorized changes, such as domain transfers or DNS modifications. The registrar must manually verify this added security measure before making any changes. This tool does not directly protect against domain shadowing, but it increases domain security in combination with other best practices.
12 Keep DNS servers and hardware updated
Regularly update and patch DNS server software and hardware to ensure highest protection against known vulnerabilities. Monitor security advisories and promptly apply security patches to minimize the risk of exploitation by attackers.
A call to action to protect your domains
In light of domain shadowing threats, it is essential for domain experts and brand managers to recognize the potential risks of this malicious technique. Domain shadowing takes advantage of the vulnerabilities in the internet and DNS infrastructure, which designers initially did not create with security in mind. Attackers exploit the trust and credibility built by others, leveraging their brand names, SEO benefits and infrastructure to deceive users. Despite being amended and updated, the DNS still possesses inherent weaknesses that allow vulnerabilities to slip through the cracks, even for well-established companies. Therefore, domain experts and brand managers must safeguard their online assets and implement robust security measures to combat the ever-evolving threats posed by domain shadowing and other cyberattacks.