DNS records | Behind domains

Deepen your expertise with our advanced guide to DNS records: A comprehensive resource crafted for seasoned DNS professionals who navigate and shape the evolving DNS landscape.
Published by

Simone Catania
Date
DNS functions as the internet’s phonebook, translating human-friendly domain names into machine-readable IP addresses. This allows users to access websites without memorizing complex numeric addresses. The seamless operation of this system hinges on a crucial element known as DNS records.
These records are essential in guiding the resolution process, acting as signposts that direct internet traffic to the correct destinations. Understanding the various types of DNS records, their specific functions and their significance is not just a matter of technical curiosity but a necessity for effective domain administration and secure internet communication.
Through this guide, you’ll not only revisit the fundamentals of DNS but also delve into the intricate details and critical role of DNS records that form the cornerstone of DNS management and architecture.
What are DNS records?
DNS records, also known as Resource Records (RRs), are structured data entries within the Domain Name System (DNS) that map domain names to IP addresses and define various types of services and configurations for a domain.
Different DNS records carry out diverse functions within the DNS, enabling the internet to translate domain names into IP addresses, manage domain aliasing, route email and more. They vary in scope, ranging from directing web traffic to specific servers, to specifying the servers responsible for email exchange for a domain.
The versatility in the types of DNS records allows administrators to precisely control how their domain’s presence on the internet is managed, ensuring efficient operation and connectivity for different services associated with their domain.
DNS records and resource records are often used interchangeably in the context of the Domain Name System (DNS), but they do have slightly different connotations: “DNS records” is a more general term used colloquially to refer to all types of data associated with a domain in the DNS. “Resource records” is a more specific term defined by the official DNS specifications (RFC 1035, for example). When discussing the technical aspects of DNS configuration or the protocol itself, “resource record” is the more accurate term.
All resource records are DNS records, but people typically use “DNS records” in a broader sense, sometimes encompassing both resource records and the concept of DNS. Resource records refer to the individual entries that conform to a specific structure within the DNS. When configuring a domain’s DNS settings, you create, delete, or modify resource records within a DNS zone file.
The role of DNS records in domain resolution
DNS records play a crucial role in the process of domain name resolution. When a user enters a domain name into their browser, the browser initiates a DNS lookup to retrieve the specific IP address associated with that domain. The lookup process starts with a query to a recursive DNS server, which then contacts a root name server. The root server directs the recursive server to a top-level domain (TLD) server (such as one for .com or .de), which in turn provides the address of the authoritative name server for the specific domain being queried.
Once the recursive server contacts the domain’s authoritative name server, it retrieves the DNS records associated with that domain. These records include various types of data essential for the domain resolution process. The DNS records are returned to the recursive DNS server, which caches the information and sends it back to the user’s browser, thus allowing it to connect to the web server associated with the IP address and retrieve the website content.
Through this streamlined process, DNS records facilitate the smooth functioning of the internet by ensuring users are directed to the desired webpage, making them crucial for accessing websites, sending emails, and more.
The structure of a DNS record
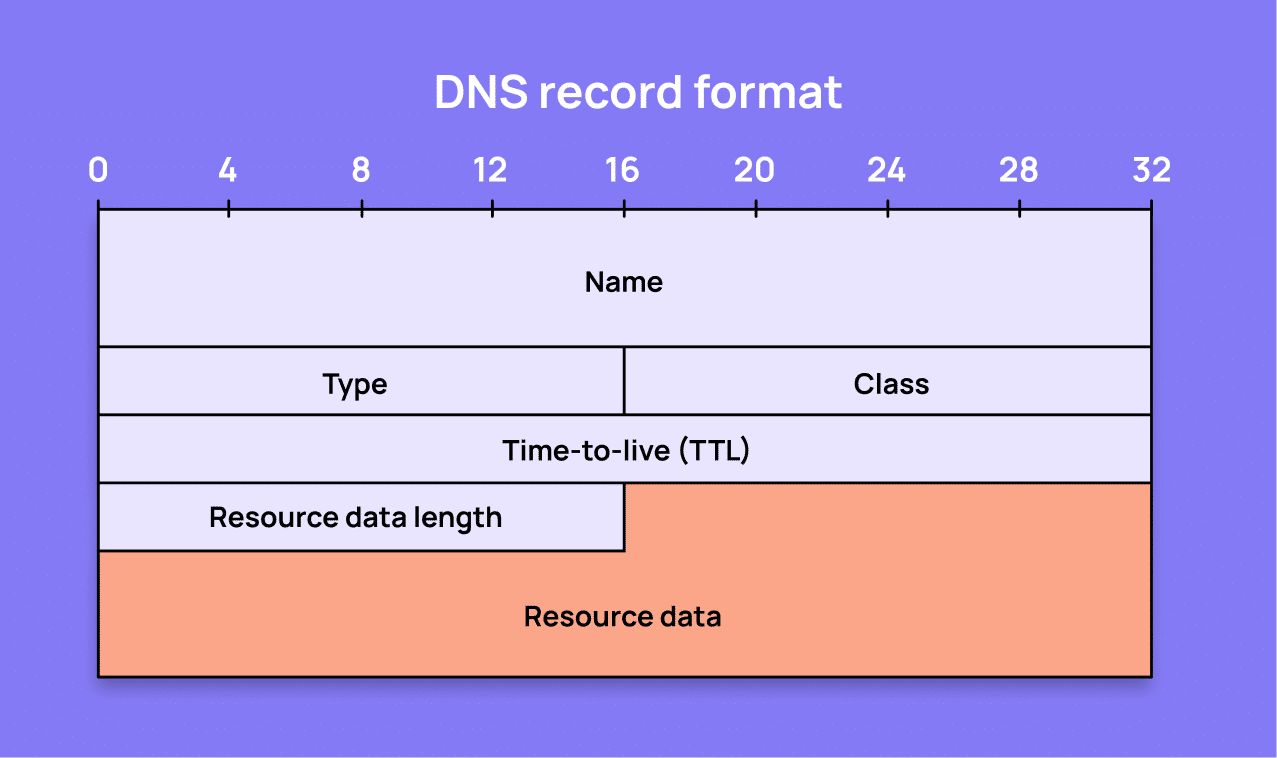
A DNS record consists of several mandatory and optional fields that define how a domain name is translated into an IP address or other information.
As defined in RFC 1035, the main components of a DNS record (resource record) are:
- Name: Specifies the domain name to which the record applies.
- Type: Indicates the type of the record (e.g., A, AAAA, MX, CNAME, NS, PTR, TXT, etc.), defining the format of the data field and its intended use.
- Class: Identifies the network’s class. Internet (denoted as IN) is the most commonly used class.
- TTL (Time to Live): The amount of time, typically in seconds, that the record is allowed to be cached by a resolver before it should be discarded or refreshed.
- RDLENGTH (Resource Data Length): The length of the RDATA field. Optional for some record types.
- RDATA (Resource Data): The data of the resource record, the format and interpretation of which depend on the type and class of the record. For example, in an A record, the RDATA field would contain an IPv4 address, whereas for an MX record, it would contain a preference value and the domain name of the mail server.
Essential DNS record types domain experts need to know
Domain professionals recognize the vast array of DNS record types, each designed to fulfill specific internet infrastructure functions. This diversity reflects the multifaceted nature of modern digital communication, necessitating distinct records for varied tasks.
Key DNS records among these are:
- A/AAAA records (Address Records) serve as the foundation of DNS. They link domain names to their corresponding IP addresses, utilizing IPv4 and IPv6, respectively, thus facilitating the crucial first step in accessing websites.
- MX Record (Mail Exchange Record) is crucial for routing emails. It directs a domain’s email traffic to the correct email servers, ensuring that communication reaches its intended destination reliably.
- CNAME Record (Canonical Name Record) is used to alias one domain name to another, manage subdomains and redirect multiple DNS requests to a single IP address, simplifying domain administration.
- TXT Record (Text Record), versatile in its utility, is employed for various purposes, from verifying domain ownership and distributing SPF data to preventing email spoofing to other server instructions, making it indispensable for domain security protocols.
- NS Record (Name Server Record) delegates a domain or subdomain to use a specific set of DNS servers, thereby designating the authoritative servers responsible for responding to DNS queries for that domain, which is fundamental for domain zone management.
- SRV Record (Service Record) identifies the location of services within a domain, such as Microsoft Office 365, SIP protocols, etc. It specifies the hostname and port number for each service, enhancing the domain’s service configuration and discovery.
- CAA Record (Certification Authority Authorization Record) is a security-oriented DNS record. It allows domain owners to specify which certificate authorities (CAs) are permitted to issue certificates for their domain. A CAA record reduces the risk of unauthorized certificate issuance, adding an essential layer of security to domain verification processes.
- ALIAS Record functions similarly to a CNAME record but can be used at the root domain level, whereas CNAME records cannot. The ALIAS record allows for the aliasing of domain names at the apex domain, making it possible to seamlessly point your root domain to another domain or hostname. It is especially useful for hosting services that require domain apex pointing without the limitations of CNAME records.
These records enable DNS experts and domain managers to fine-tune the domain’s navigation, email services, security measures and service protocols, fortifying the sophisticated architecture that keeps the digital world interconnected and secure.
| Record type | RFC | Function | Description | Relevant information |
| A | RFC 1035 | Address mapping | Maps a domain to a 32-bit IPv4 address, facilitating the primary connection between the domain name and the server where the website is hosted. | Critical for basic DNS operation; used for IPv4 addresses. |
| AAAA | RFC 3596 | Address mapping | Maps a domain to a 128-bit IPv6 address, enabling the connection between the domain name and the server where the website is hosted in the IPv6 architecture. | Essential for modern DNS operation; supports the newer IPv6 address space to accommodate the growing need for more internet addresses. |
| MX | RFC 1035 | Mail exchange | Directs email to the correct email server(s) for a domain, specifying the priority of each server for receiving mail. | Priority is indicated by a preference number; the lower the number, the higher the priority. |
| CNAME | RFC 1034 | Canonical name | Aliases one domain name to another, allowing multiple domain names to map to the same server IP address without additional A or AAAA records. | Often used for subdomains, like ‘www’ or ‘mail’. |
| TXT | RFC 1035, RFC 7208 | Text information | Provides text information to external sources, commonly used for specifying sender policy framework (SPF) data, domain ownership verification and other security notes. | Versatile record for various verification processes. |
| NS | RFC 1035 | Name server delegation | Delegates a domain or subdomain to a specific set of DNS servers, indicating the authoritative name servers responsible for a particular DNS zone. | Essential for DNS zone management and delegation. |
| SRV | RFC 2782 | Service locator | Specifies the location of services, including the hostname and port number for certain services within domains, like email or VoIP. | Utilized for service discovery and specific protocol configurations. |
Obsolete DNS records
Over time, the evolution of the internet and its technologies has led to some DNS record types becoming obsolete. Once integral to various functionalities within the DNS, these records have fallen out of use for multiple reasons, including technological advancements, the development of more secure or efficient alternatives or changes to internet protocols and practices.
For instance, the A6 record initially intended to aid in the transition to IPv6 by specifying IPv6 addresses, was made obsolete by the more straightforward AAAA record. Similarly, SIG (Signature) records were superseded by RRSIG records with the advancement of DNSSEC, offering improved security features for DNS data. The DNAME record, although not marked as obsolete, has seen limited use due to its complexity and potential to confuse DNS administrators.
Each obsolete record type represents a step in the ongoing evolution of internet infrastructure, reflecting technological shifts and how we use the internet. As newer technologies emerge and standards evolve, certain DNS record types may no longer be compatible with current needs, leading to their classification as obsolete DNS records. For example, with the rise of ALIAS records providing enhanced functionality, traditional CNAME records could potentially phase out.
The scopes of DNS records
DNS records perform several critical functions with different scopes. Below is a table categorizing various DNS records according to their primary function scope. This classification helps understand which DNS records are important for different purposes, such as domain resolution, mail handling, security and other domain-specific configurations.
| Category | DNS record type | Purpose/function |
| Domain resolution | A (IPv4Address) | Maps a domain to an IPv4 address. |
| AAAA (IPv6 Address) | Maps a domain to an IPv6 address. | |
| CNAME (Canonical Name) | Redirects one domain to another domain (aliasing). | |
| Mail handling | MX (Mail Exchange) | Directs mail to an email server configured to receive it. |
| TXT (Text) | Generally used for email security settings (SPF, DKIM, DMARC). | |
| Security | TXT (Text) | Can also be used for Google site verification, etc. |
| DNSSEC (DNS Security Extensions) | Adds a layer of security by validating responses to DNS lookups. | |
| Service configuration | SRV (Service Locator) | Identifies services like VOIP, SIP, IM and others. |
| CAA (Certification Authority Authorization) | Specifies which CAs can issue certificates for a domain. | |
| Other configurations | PTR (Pointer) | Maps an IP address to a domain, primarily for reverse DNS lookups. |
| NS (Name Server) | Designates the authoritative name servers for the domain. | |
| SOA (Start of Authority) | Provides essential domain information like email contact and refresh rate. |
DNSSEC and DNS records
The traditional DNS does not inherently include security features to safeguard against certain types of attacks, such as cache poisoning or spoofing, by which an attacker can redirect traffic to malicious sites. This is where DNSSEC, or DNS Security Extensions, comes into play. DNSSEC adds a layer of security to DNS lookup and exchange processes by enabling DNS responses to be digitally signed.
By validating these digital signatures, DNSSEC ensures the authenticity of the source DNS records, confirming that they have not been tampered with during transit. Essentially, while DNS records provide the necessary mapping for internet navigation, DNSSEC certifies that this mapping is accurate and trustworthy, enhancing the security and reliability of the domain name resolution process.
The implementation of DNSSEC to enhance the security of DNS records introduces several specific types of DNS records. Key among them are:
- The DNSKEY record holds the public key that corresponds to a private key used by the domain owner to digitally sign their DNS records.
- The RRSIG record contains the cryptographic signature that can be verified using the DNSKEY to ensure the authenticity of the response.
- The DS (Delegation Signer) record is used to establish a chain of trust. It contains the hash of a DNSKEY record and is placed in the parent zone e.g. at the TLD registry to vouch for the integrity of the child zone’s key.
- Lastly, NSEC and NSEC3 records provide authenticated denial of existence, ensuring that a given name does not exist in the zone. They differ in their approach to prevent zone walking, with NSEC3 utilizing hash functions to obfuscate the domain names, offering additional security.
These DNS records facilitate the DNSSEC protocol’s objective of securing domain name resolutions by preventing attacks such as data spoofing and cache poisoning.
How to manage DNS records
Managing DNS records is a fundamental aspect of maintaining your domain’s presence on the internet. Through a domain registrar such as InterNetX, accessing and adjusting these parameters can be streamlined via tools like AutoDNS.
AutoDNS simplifies the navigation through your domain’s DNS settings and offers a user-friendly interface for performing various DNS management tasks.
To add, edit or remove DNS records, log into your AutoDNS account and select the domain you wish to modify. You will then have the option to navigate to the DNS settings section, where you can add new resource records by specifying the type (A, MX, CNAME, etc.), entering the required details and saving your changes. Editing existing records follows a similar process, allowing for adjustments to ensure your domain’s services run smoothly. Removing a record is just as straightforward, with prompts to confirm deletion to avoid accidental loss of crucial configurations.
AutoDNS offers a bulk update of resource records across various zones, which includes features such as search and replace. This functionality allows for efficient management and modification of DNS settings on a large scale.
Adherence to best practices is vital when managing DNS records. Always double-check your entries for errors and understand the impact of changes on your domain’s accessibility and security. A backup strategy for your DNS settings can mitigate accidental deletions or misconfiguration risks. AutoDNS performs basic checks on the resource records to improve accuracy and offers a feature for “Zone History,” which includes historical zone data, enabling easy restoration in case of any issues or errors. By utilizing AutoDNS, you can ensure your DNS management process is efficient and secure, keeping your domain’s operations running without any hitches.
Who is responsible for DNS records?
Managing DNS records is primarily the responsibility of the domain owner and their domain registrar or DNS hosting provider. When a domain is registered, the owner can configure its DNS records through a control panel provided by the registrar or a third-party DNS hosting service. Larger organizations may have dedicated IT departments or specialists to handle DNS configurations and ensure that records are set up correctly and maintained.
On a higher level, the authoritative DNS servers, usually managed by the hosting provider or the organization itself, hold the DNS records and respond to queries from recursive DNS servers worldwide. Additionally, root name servers and TLD servers play a crucial role in the overall DNS infrastructure, but the domain owners directly manage individual DNS records of domains through their hosting providers or domain registrars.
The collaboration between these entities ensures that DNS records are accurately propagated and accessible across the internet, facilitating the resolution of domain names into IP addresses.
DNS records for domain resellers
Domain resellers, who purchase domain names in bulk from registrars to sell to end users, can utilize DNS records in several strategic ways to add value and streamline their operations.
Here’s how:
-> Custom DNS services: Resellers can offer managed DNS services, such as virtual nameservers, as an additional feature to their customers. This involves handling the setup, management and maintenance of DNS records on behalf of their clients, which can be especially attractive for businesses without the technical expertise to manage DNS themselves.
-> White-label solutions: Using CNAME and/or ALIAS records, domain resellers can provide white-label services, allowing clients to use their brand names on reseller products. For example, a domain reseller can enable a client to point mail.clientdomain.com to a white-labeled email service they provide.
-> Enhanced security features: Resellers can configure DNSSEC for their domains, providing added security by protecting the internet infrastructure from certain attacks such as cache poisoning. This can be a selling point for clients concerned about security.
-> Performance and reliability: Implementing advanced DNS records, such as multiple A or AAAA records for load balancing and redundancy, can improve the services offered under the domain names sold. This can increase customer satisfaction and reduce churn.
-> Rapid propagation: By setting appropriate TTL values for different types of DNS records, resellers can manage how long DNS caches store information, which can help faster propagation of changes and reduce downtime when transitioning services for their customers.
-> Email services: By configuring MX records, resellers can direct the domain’s email traffic to specific mail servers. This is essential for providing email hosting services under the sold domains.
Domain resellers can provide added value to their services with DNS records, enhance customer trust and differentiate themselves in a competitive market. This not only strengthens customer retention but can also attract new clients looking for comprehensive and secure domain solutions.
Common problems and solutions with DNS records
Common problems with DNS records include propagation delays and misconfigurations, which can lead to website inaccessibility, email delivery issues and other network-related problems.
Propagation delays are a natural part of the DNS record update process, sometimes taking up to 48 hours, as changes need to be disseminated across the internet’s various DNS servers. To address propagation delays, patience is key. However, verifying that the correct information was entered at the outset can save time.
Misconfigurations, however, can range from incorrect IP addresses in A records to improper MX record setups. This can lead to more complex issues that impede your domain’s functionality. To ensure accuracy, inspect the records for obvious mistakes and consult your hosting provider’s documentation.
Tools like nslookup and dig are invaluable for troubleshooting DNS issues. nslookup can check DNS records of the queried domain name. Similarly, dig offers a more granular look at the DNS resolution process, giving detailed information about each queried DNS record. Alternatively, you can use online services like MXToolbox or Google’s dig web interface. These allow you to enter the domain and select the DNS record type you wish to query without using command-line tools. Utilizing these tools, you can quickly verify if DNS changes have propagated or identify misconfigurations, facilitating prompt corrections and mitigating the impact on your domain’s operation.
Nslookup vs dig
dig (Domain Information Groper) and nslookup (Name Server Lookup) are both command-line utilities used to query DNS servers. They are available on most Unix-based operating systems, including Linux and macOS, and nslookup is also available on Windows.
These tools are commonly used for troubleshooting DNS problems and to obtain detailed domain-related information.
Feature dig nslookup Full Name Domain Information Groper Name Server Lookup Purpose DNS troubleshooting and queries DNS troubleshooting and querying for DNS record information Output More detailed and technical; includes query time, server used, and more Less detailed by default but can be toggled to be more verbose Flexibility Highly flexible with extensive options for detailed queries Has interactive mode and a limited non-interactive mode Batch usage More suited for scripting and batch operations Not traditionally used for batch operations Maintained Actively maintained and updated No longer actively maintained; some versions discouraged by Microsoft Usage complexity Typically more complex and preferred by advanced users Simpler to use, more user-friendly for beginners Keep in mind that nslookup is considered to be deprecated by some in the Internet Systems Consortium, although it remains available and in use on many systems, while dig is typically recommended for more sophisticated DNS troubleshooting purposes.
Understanding DNS Records
DNS records are not merely technical elements of internet infrastructure but critical components of domain and web security. They enable precise control over domain email authentication, safeguard against phishing and spoofing attacks, and ensure users access the intended destination securely. Proper configuration, regular updates and the deployment of DNSSEC are essential practices in protecting a domain against cyber threats, maintaining website integrity, and preserving digital trust.
To navigate the complexities of DNS management and tackle more challenging issues, consider consulting our IT professionals at InterNetX. Their expertise can provide guidance and peace of mind. Additionally, subscribing to the InterNetX blog or newsletter is recommended for anyone seeking to stay informed on the latest insights and best practices in DNS management and web security. This commitment to ongoing education is crucial in the ever-evolving landscape of internet technology and cybersecurity.